
A massive SMS spamming operation kicked out tens of millions of text messages, pestering unsuspecting recipients with links to fake sites flogging loans and free money.
The operation was simple but smart. The system processed vast batches of phone numbers and curated custom messages on the fly with links to the fake sites. These fake sites urged spam victims to sign up with their name, email address and phone number and promised “free money… for real.” (It wasn’t.) Sometimes confused victims would message the spam number back. If the system spotted certain keywords, like “report” or “FCC,” their number would be added to a “stop list” so they wouldn’t be bothered again.
It’s almost as if the spammers thought of everything. Except, that is, putting a password on their server.
Security researcher Bob Diachenko found the spam-sending database on an exposed server last month. He shared a portion of the data with TechCrunch. He also wrote up his findings. By coincidence, the server was pulled offline before we could reach out, but we still had time to look at the inner workings of the SMS spam operation.
And we knew exactly whom to contact — because the spam operators’ email addresses were listed as “admins” in the database.
“This incident raises the issue once again that data security can affect legitimate businesses and what many would consider ‘gray marketing’ at best,” said Diachenko.
The database is run by an outfit called ApexSMS. Little is known about Apex — it’s not known if it’s a legitimate company or not. Its website today is simply a login page, but for a time simply said, “nothing to see here.”
What is known is that ApexSMS, the name of the database on the exposed server, spammed millions of cell phone numbers with varying messages, all pushing their victims to dozens of different scam sites.

An example of the kinds of spam SMS messages sent (Image: TechCrunch)
ApexSMS relies on Mobile Drip, a “high-volume SMS” messaging and marketing platform. (A Mobile Drip subdomain points directly to ApexSMS’ login page.) Mobile Drip, which debuted in February, says it allows customers to use its platform to send pre-written messages that autoreplies with the next message and broadcasts messages — where the customer sends a single message in bulk.
The company’s sign-up form suggests the company can allow customers to send more than five million SMS messages each month — if they pay for it.
In all, the exposed database contained 80 million records — so-called leads, which marketers use to pitch products and services — which included people’s names, locations, phone numbers and IP addresses. It also contained cell phone numbers and their carrier network name.
Of the estimated 38 million messages sent through disposable toll-free phone numbers, 2.1 million victims clicked on the link in the message.
The database even kept track of who clicked on which message through Grand Slam Marketing, one of the alleged companies involved in the operations, which was named a “premium parter” on one of the scam sites victims were pointed to.
Other scam sites — like copytm.com — contained hidden code that scraped the name, email address, phone number and IP address and submitted it to ApexSMS’ spam database.
Dozens of other scam sites existed in the database.
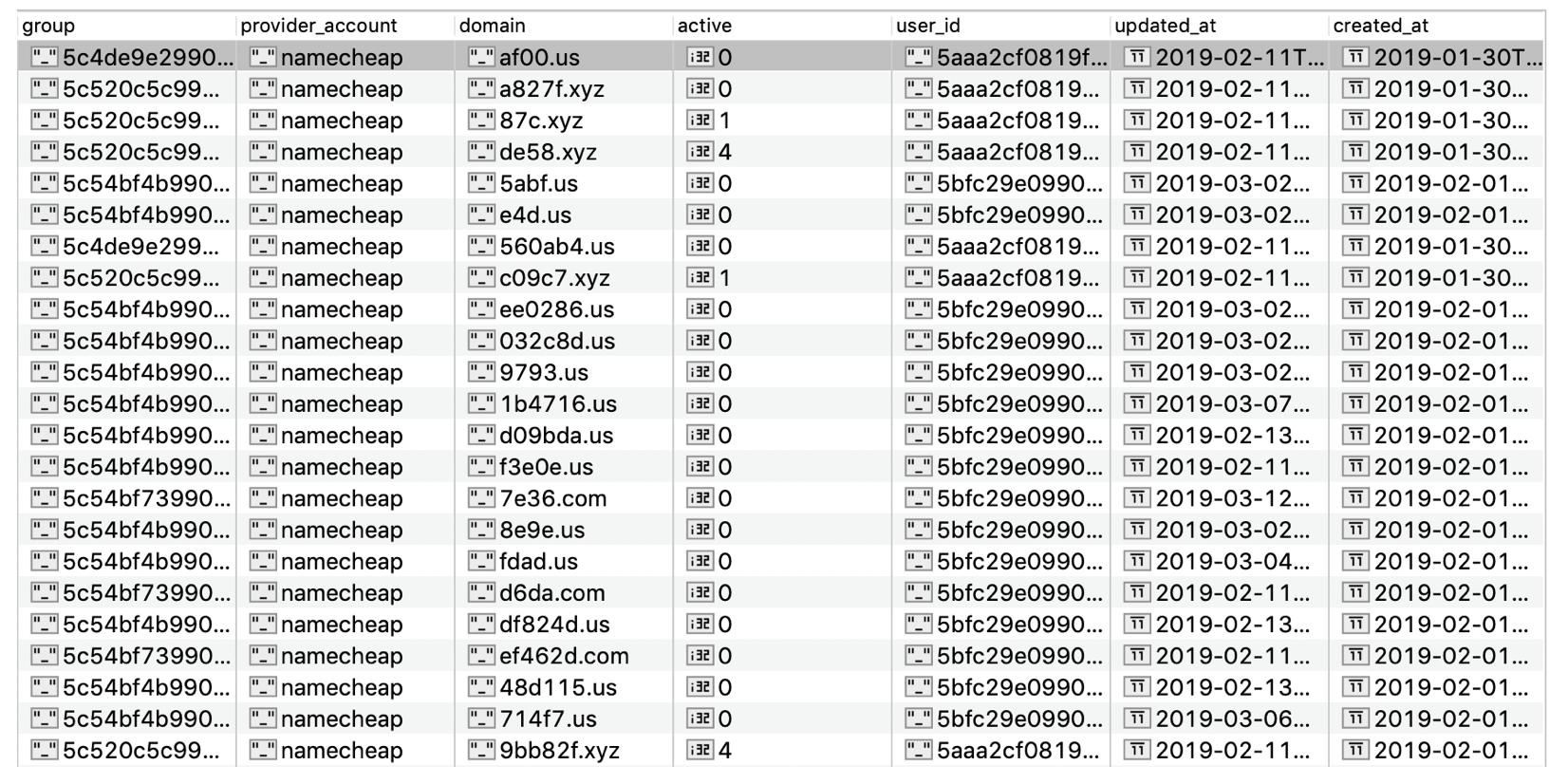
Many of the scam domains used in the spam campaign (Image: TechCrunch)
The database also recorded when victims replied. More than 115,000 people responded to spam messages. “Wrong number,” said a few. “Who is this,” said others.
When one spam message said, “this is what we was talking about last night” with a scam link to try to trick the user into tapping, the database recorded the clearly frustrated reply. “Nathan is married and didn’t talk to you yesterday because I his wife had this phone. Text this phone I’ll have you charged with harassment,” the entry read.
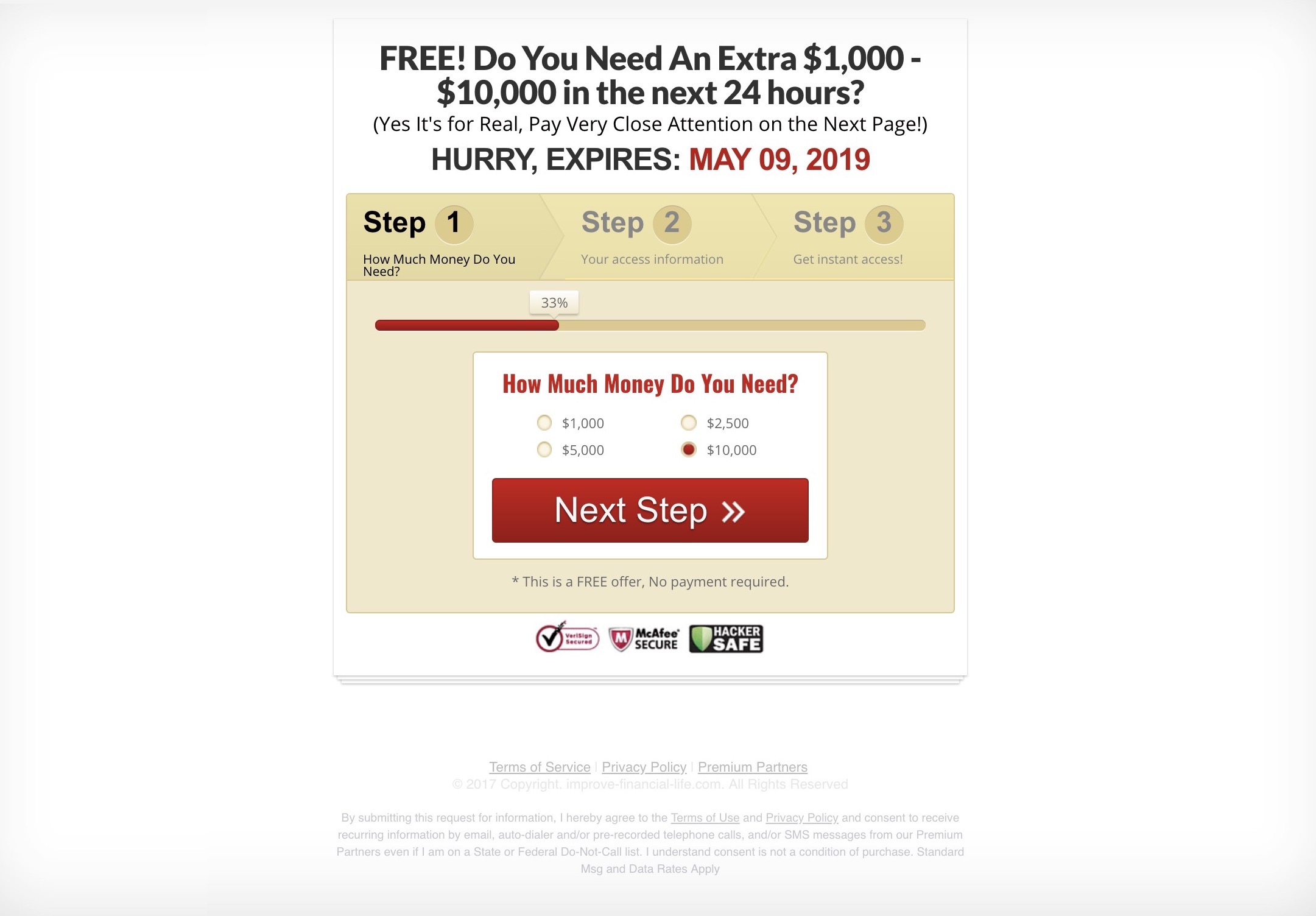
One of the scam websites (Image: TechCrunch)
We sent several emails to ApexSMS and the operators found in the database but did not hear back. When reached, a statement from Mobile Drip said:
“Mobile Drip is an SMS platform for businesses that gives a customer the ability to send SMS messages to their opt-in leads and customers, as well as track the results of their marketing campaigns,” said the statement. “Mobile Drip has clients from many different industries and all of them are required to adhere to strict guidelines on message content, as well as TCPA compliance,” referring to federal telemarketing rules.
In follow-up questions, Mobile Drip denied any connection to ApexSMS, and referred to the company’s terms and conditions, which expressly prohibit spam on its platform.
“We take compliance and data security very seriously, and we are currently investigating to determine to what extent our information has been exposed to unauthorized parties. We have currently engaged an outside legal firm to assist with our investigation of this matter and we are also engaging a cyber security firm to perform a security audit,” the company said.
“Our servers have always been password protected, so any information that may have been acquired was done so through illegal means with the goal of harming the reputation and financial success of the business,” said the company. TechCrunch disputes this claim.
Although we know the identities of the spammers, we are choosing not to publish their names. Although we’re confident in saying this is a spam operation, it’s for the courts to decide if it’s unlawful.
Most of the names in the database are associated with either ApexSMS, Mobile Drip, Grand Slam Marketing or a few other smaller advertising and marketing companies. It’s not known who was an active participant in the spam operation.
One of the named “admins” in the database, who we are also not naming, claimed he was a contracted developer but declined to comment to TechCrunch citing a non-disclosure agreement with ApexSMS. The former contractor was identified by his email address and credentials for Cloudflare, which protects sites against cyberattacks and provides site privacy, found in the database.
It’s also not known for how long the database was exposed or if anybody else accessed the database.
Regardless of the motives or the legality of the operation, Diachenko said these spammers were “still using and improperly storing the information or data of millions of people.”
Read more:
Got a tip? You can send tips securely over Signal and WhatsApp to +1 646-755–8849. You can also send PGP email with the fingerprint: 4D0E 92F2 E36A EC51 DAAE 5D97 CB8C 15FA EB6C EEA5.

