You probably have your credit card and other payment information keyed into at least 10 different services right now, all of which are likely based over a mobile app or website. For a long time, the effective user detection has been the preserve of large payment providers and web services — take Amazon.com or Google’s Gmail service as examples. Castle, part of Y Combinator’s Spring 2016 class, is the latest in a handful of companies to bring this capability to everything else.
What makes Castle, whose four-person team is split between Mountain View, California and Northern Sweden, interesting is how seamlessly the product can be integrated by clients. All they need to do to set up the Castle service is drag and drop a snippet of JavaScript code into the header of their site’s raw HTML code. Castle does the rest, from flagging suspicious logins and other nonstandard login activity, to integrating with a customer service system, to automatically suspending accounts and notifying users about a potential compromise.
The inspiration for Castle came out of the co-founders’ previous startup, payments company SettleBox, says Johann Brissmyr, Castle’s CEO.
“We worked with integrating a lot of these enterprise [security] solutions, which are now our competitors,” he says, adding that the lack of good tools to protect users gave Castle the opening it needed.
User-friendliness and setup time are a big part of Castle’s product, and the team took inspiration from analytics platform Mixpanel and Google Analytics in the realm of user interaction.
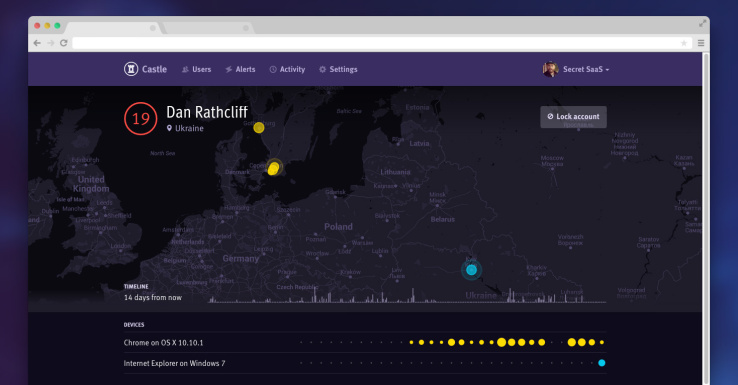
Behind the scenes, Castle works by tracking user behavior to identify suspicious activity, from behavior ranging from new locations or devices to activity considered “abnormal” by a particular user or on a particular service.
“We track every page view. We track events like login and password changes,” says Brissmyr. “Really, we’re trying to find anomalies.”
Castle, in a nutshell, looks at similar data to what popular web services like Facebook and Google seek out to identify suspicious behavior that would suggest hijacks or brute-force logins.
Similar to peer products used by other companies, Castle also assigns a “risk score” to each individual anonymized user, with different degrees of events raising or lowering that score.
For example, Brissmyr explains, customers using the same device in a different place wouldn’t raise their risk score, but their score would rise if a new device in a different location was used in a login attempt.
“We also keep track of what normal behavior is on a website,” he added. “If most users only use one mobile phone, and someone logs in from another mobile phone that raises the risk.” (The company says that among the other data it uses are Tor exit nodes, blacklisted IPs, and data center IPs that could indicate that someone has set up a proxy on AWS. “We scrape external sources and compromised databases, and if we have users matching those emails, we can check if those users were compromised on other platforms,” Brissmyr says.)
While Castle has few direct competitors, including Boise, Idaho-based security provider Kount, larger web service providers like Google or Amazon that are moving into the space could spell trouble.
Brissmyr, for his part, is confident in the face of the potential threat. “I don’t think they [Google and other web services providers] will [compete with Castle], and if they would, they would not focus as hard as we do on this,” he says. “We have made the service integrated into so many apps.”

