Apple, seen as a bastion of privacy and security, has boxed itself into a corner.
Last year, the company pushed back on a court order that demanded it build custom software that would crack the encryption on a terrorist’s iPhone. Apple refused, arguing the precedent could be used again on other devices, potentially putting all iPhones at risk. The company had mixed but strong political and legal support in favor of its case, and the matter went to court. The day before a critical hearing, the FBI dropped its case when it found hackers able to access the data in spite of Apple’s refusal.
Then, this week, Apple acquiesced to China’s demands to remove almost every VPN provider — used to bypass China’s strict online censorship — from the country’s app store, following a change in the law.
ExpressVPN said in a statement it found Apple’s decision “surprising and unfortunate”, while StarVPN said in a tweet that the move sets a “dangerous precedent” that could allow other countries to follow suit.
There was confusion and anger. Why will Apple fight a court order against a particular device when it pulls VPN apps for human rights activists in China? How can Apple argue that the FBI breaking into a single iPhone is more detrimental to user security than reducing the security for an entire country?
These are fair questions for the company, which outwardly prides itself on providing privacy and security and reacts strongly when the UK, Australia, and others are on the verge of threatening its values.
“WE FOLLOW THE LAW”
For more than a year, China has warned VPN providers that they would need a state-sanctioned license to continue operating. Beijing is on an information crackdown ahead of the Chinese leadership reshuffle, expected later this year, because VPNs are used to skirt the country’s so-called “Great Firewall” state censorship.
China’s information ministry finally enacted the rule on July 30, making the majority of VPN services illegal in the country overnight — forcing Apple to act or face consequences.
Apple boss Tim Cook defended the move on a post-earnings call on August 1, saying the company would rather not remove the apps, “but like we do in other countries, we follow the law wherever we do business.”
There’s a great sense of unease and mixed feelings on what Apple should have done — stand up to Beijing, profits be damned or not — and every argument seems to have an equally compelling counterpoint.
China makes up some 17 percent of Apple’s revenue — about $8 billion — as of its third-quarter earnings. But with that figure in double-digit decline year over year, Apple can’t afford not to play ball in the region. Where Western companies fail, Chinese companies often pick up the slack. Apple also recently opened a data center in the country to comply with China’s new cybersecurity rules, reaffirming its commitment to the region.
The other argument is that pulling out of the region would leave millions stranded with phones that can no longer access cloud-based and messaging services built into the phones. Is Apple willing to give up billions in revenue and isolate its customers for the sake of a few VPN apps? In any case, any criticism or rebuke from Apple wouldn’t change Beijing’s mind. Instead, it would likely antagonize the situation with a world power that doesn’t take well to criticism.
Given the circumstances Apple found itself in last year when it launched a legal fight against the FBI over the San Bernardino shooter’s phone, many have reacted angrily to its apparent about-face.
Cook denied that criticism, arguing that China’s new policy and the FBI case last year are “very different,” because the law in the US supported Apple’s legal fight.
Cook is right in that the US at least has due process, but the company’s legal battle was in the end largely superficial and resolved without any determination on whether the FBI’s demand was lawful. The FBI got what it wanted, and yet Apple’s values of privacy and security were upheld and appeared stronger than ever.
What seems to be a utilitarian approach for its Chinese customers falls foul of the company’s global privacy and security mantra, something the company doubled-down on in its fight against the FBI last year.
And that sets a dangerous precedent going forward, as noted by The New York Times.
TOO DANGEROUS FOR PUBLIC CONSUMPTION
First there was China banning VPNs, but what happens in Beijing rarely stays in Beijing. Russia will also ban VPNs later this year and it’s only a matter of time before other countries get similar ideas.
In fairness, other companies haven’t escaped harsh security policies. Several other messaging apps, including Weibo and WeChat, were censored in China, and LinkedIn was banned in Russia after it refused to store customer data in the country. Google hasn’t operated in China for years after its search engine was censored, and Amazon also had to ban VPNs from its Chinese cloud.
The big question is what happens when Apple (or any other company) faces this inevitable dilemma again.

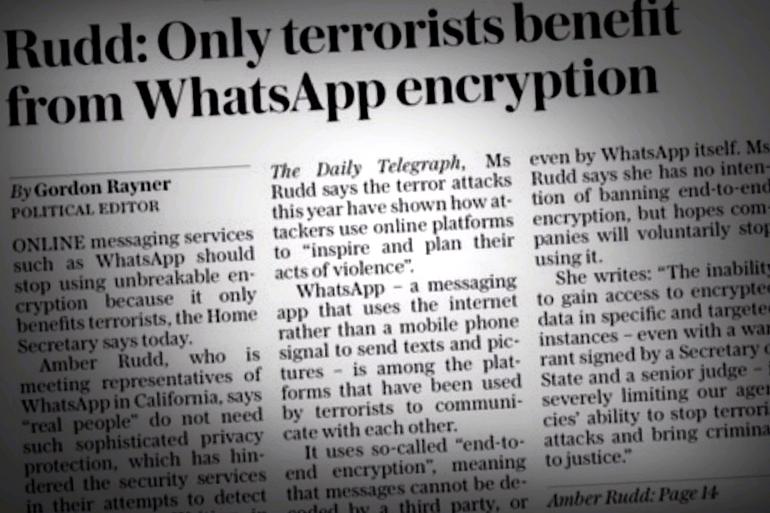
UK home secretary says “real people” do not need end-to-end encryption. (Image: file photo)
“If Apple and others will sacrifice user access to crucial security services at the behest of governments like China and Russia, it raises significant new questions about if and how they will react when the UK and Australia order the insertion of back doors or other security flaws,” said Amie Stepanovich, US policy manager at digital rights group Access Now, in an email.
The UK and Australia are set to be the next major battleground to test Apple’s resolve. With a fraction of the population compared to the US or China, the financial stakes are far lower, making Apple’s response less predictable.
The UK has been on a political crusade against end-to-end encryption for years. It has escalated in the past few months following a string of deadly terrorist attacks London and Manchester.
This week, home secretary Amber Rudd called encryption a “problem”. It’s part of a coordinated push for greater surveillance powers to access encrypted content and prohibit companies from introducing end-to-end encryption, on top of the “snoopers’ charter” that was recently passed, seen as the “most extreme surveillance law ever passed in a democracy” by Jim Killock, executive director of the Open Rights Group.
The reality is that today, tomorrow, or the next day, the UK could deem Apple’s messaging and video calling services iMessage and FaceTime — which were “designed from the ground up to only work using end-to-end encryption” — too dangerous for public consumption. (“There is no ‘off switch’ for iMessage encryption,” said John Gruber, an Apple reporter, in a blog post. The government would have to block the service.)
Australia’s prime minister is also pushing for greater decryption powers, even if that means defying the laws of mathematics.
It’s hard to paint a bright and prosperous future with a dark cloud lingering.
“Wouldn’t companies push back against such demands — possibly — but it’s a much harder fight to win if it’s not just the UK making the demand, but an international coalition of governments putting pressure on them to obey the same powers,” said Danny O’Brien, international director at the Electronic Frontier Foundation, referring to the Five Eyes surveillance coalition, made up of five key allies including the UK and Australia.
“This, it seems is what [Theresa] May’s government wants next,” he said.
It’s only a matter of time before the UK or Australia — or another Western power with a controversial, unabashed, and impulsive leader — makes the same request that China did, or greater.
“When these companies bow down to repressive laws and governments, they are failing their users and everyone their tools or systems impact,” said Stepanovich.
It’s not one rule for the US and another for China — the lowest common denominator will prevail.
And so when Apple and other companies comply with the small but pinching laws laws of today, they have little choice but to accept the greater, more punishing laws of tomorrow.

