
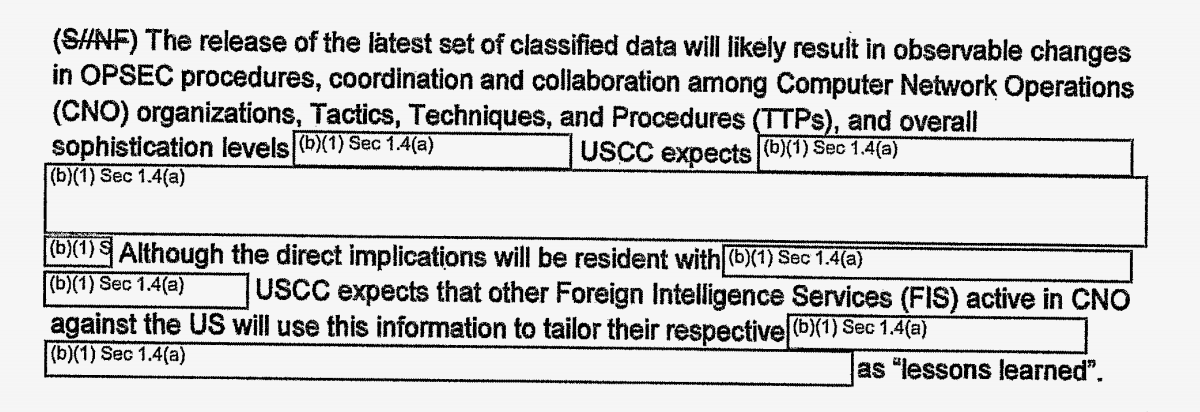
A previously secret document from 2010 warned that classified diplomatic cables published by WikiLeaks would likely result in “observable changes” in the tactics and techniques used by foreign spies, potentially making it easier to avoid detection by U.S. agencies.
The document, recently declassified through a Freedom of Information request by the non-profit National Security Archive and shared with TechCrunch, reveals a rare glimpse inside U.S. Cyber Command, the military’s main cyber-warfare unit, which feared that the leaked diplomatic cables of communications between U.S. foreign embassies would uncover and hamper its ongoing offensive cyber operations.
Michael Martelle, a research fellow for the National Security Archive’s Cyber Vault Project, said the subsequent publication of the cables by WikiLeaks gave the adversaries a “period of heightened advantage.”
The publication of the document comes almost exactly a decade after U.S. Army intelligence analyst Chelsea Manning downloaded and forwarded 750,000 classified cables to leak-publishing site WikiLeaks. Manning was subsequently sentenced to 35 years in prison for what was then the largest leak of U.S. classified material in its history. Her sentence was commuted by then-president Barack Obama in 2017.
Cyber Command wrote its findings in a so-called situational awareness report dated December 2010, just days after The New York Times and several other news outlets published the full cache of diplomatic cables, albeit with redactions to protect sources. The highly redacted assessment warned that the military cyber unit expected to see foreign intelligence services active in cyber-espionage against the U.S. to “use the information” published by WikiLeaks to their own advantage.
(Image: National Security Archive)
According to the assessment, the leaked cables “clearly state” that the U.S. government entities at the time “have knowledge” of specific tactics and techniques used by foreign adversaries, including “malware, toolsets, IP addresses, and domains used in intrusion activity.”
It went on to warn that those same adversaries are “expected to modify their current infrastructure and intrusion techniques” to evade U.S. cyber-defenses.

(Image: National Security Archive)
Although the redactions in the declassified document makes it unclear exactly which adversaries Cyber Command was referring to, Martelle said that only one specific adversary — China — was mentioned in the entire cache of unredacted documents, which Wikileaks published a year later, much to the chagrin of the news outlets.
Just one month before the first cables were published, Google had publicly accused Beijing of launching targeted cyberattacks against its network. Several other companies, including antivirus maker Symantec and defense contractor Northrop Grumman, were also hit by the attacks, in an offensive cyber campaign which became known as Operation Aurora.
Google subsequently withdrew from China following the furore.
Cyber Command’s assessment said that all Dept. of Defense divisions and U.S. intelligence agencies “remain vigilant” to anomalies amid fears that its adversaries will “leverage this new information” to “further their cyber initiatives.”
When reached, a spokesperson for Cyber Command did not comment. Google also did not comment. An email to WikiLeaks went unreturned. WikiLeaks founder Julian Assange is currently detained and awaiting extradition to the U.S. for publishing the classified cables.

